WordPress Security Guide: 20 Best Practices for Keeping Your Website Secure
Picture this:
You open your WordPress site, all bright-eyed, bushy-tailed, and ready to upload your latest blog post…only to be met by a bunch of weird content directing people to buy pharmaceutical pills from sketchy websites.
It’s most webmasters worst nightmare, but it’s something that can happen to your WordPress site…if you don’t put in place the right security best practices.
We’re not trying to scare you – WordPress is secure. It has a dedicated security team and an army of knowledgeable contributors and developers to help keep it that way.
But if you aren’t building on that secure foundation by following WordPress security best practices, you could be opening the door for malicious actors to get their fangs into your website.
In this post, we’re here to help you learn what those best practices are so that you can stop that nightmare scenario from becoming a reality.
To that end, we’re going to cover the following sections:
In This Article
- Is WordPress Secure?
- Why You Shouldn’t Wait to Get Serious About WordPress Security
- 20 Things You Can Do Right Now About WordPress Security
- 1. Understand Basic WordPress Security Themes
- 2. Promptly Apply WordPress Updates
- 3. Use Strong Passwords for Everything
- 4. Use Trusted Plugins
- 5. Secure Your Computer
- 6. Lock Down Your Login Page
- 7. Take Regular Backups
- 8. Use Secure Hosting
- 9. Install an SSL Certificate and Use HTTPS
- 10. Use SFTP and Don't Store Passwords
- 11. Disable XML-RPC
- 12. Disable File Editing
- 13. Monitor for Security Issues
- 14. Secure Key WordPress Files and Folders
- 15. Implement Proper File Permissions
- 16. Consider Activity Logging
- 17. Add the Latest Security Headers
- 18. Secure Your Database
- 19. Disable Hotlinking
- 20. Set Up DDoS Protection in Advance
- What Are the Risks When a Site Gets Breached?
- How to Tell If Your WordPress Site Has Been Hacked
- Three Best WordPress Security Plugins and Tools
- Focus On These Three Things for the Biggest WordPress Security ROI
- Monitoring, Identifying, and Fixing WordPress Security Breaches
While it might take you a couple of hours to work through the best practices in this post, that small investment now will pay dividends in the future in the form of a secure, bulletproof WordPress site.

We rigorously test and research every product that we recommend through HeroThemes. Our review process. We may also earn a commission if you make a purchase through our links.
Is WordPress Secure?
WordPress powers over 43% of all the websites on the internet, which means it’s a juicy target for malicious actors.
The fact that WordPress is so popular also means it’s used by a wide variety of people, including people with vastly different knowledge levels. Think an experienced developer vs someone who’s just launching their first blog…and everyone in between.
There’s good news and bad news here…
Good news:
WordPress is secure. That’s why it’s used by so many regular people, as well as big organizations like the US White House and Facebook.
Facebook and the White House wouldn’t trust their websites to an insecure platform. What’s more, 43% of the websites on the Internet wouldn’t run on WordPress if it weren’t secure.
Bad news:
A lot of WordPress sites do get hacked. In Sucuri’s hacked website reports, WordPress is routinely the most hacked platform (remember – it’s super popular).
So – how can WordPress be safe and also have sites hacked? Aren’t those mutually exclusive things?
Well, the answer is entirely in how people use WordPress.
If you’re proactive about following security best practices, like those we’ll cover in this post, you can keep your WordPress site secure and avoid issues.
WordPress has a large security apparatus in place, including an official 50+ member security team and an array of experienced developers who build secure extensions and flag potential issues.
Those people do a great job of making WordPress secure – but you still need to do your part if you want to keep it that way.
If you don’t build on the hard work of those WordPress contributors and follow best practices, you can make mistakes that open up holes in the WordPress software, whether that’s using a weak password, installing a vulnerable plugin, or something else.
Why You Shouldn’t Wait to Get Serious About WordPress Security
WordPress security is one of those things that feels like it’s not a big deal…until it’s a really big deal.
You have a lot of things on your plate in terms of marketing and growing your site, so it’s easy to push security to the back because it’s hard to tie making security improvements to growth metrics like traffic or revenue.
We’re being a little blunt here, but that line of thinking is incredibly shortsighted. Implementing the WordPress security checklist below takes some time and potentially a little money, but those costs pale in comparison to what you’ll “pay” if your site is breached.
One security breach will easily “cost” you more in terms of lost time, revenue, SEO traffic, and trust with your visitors.
Basically, you don’t want to gamble with your site’s security. Put in the time now to protect yourself from a huge cost later on.
20 Things You Can Do Right Now About WordPress Security
So far, we’ve talked about theory. Now, let’s start pivoting into some actionable tactics for locking down your site, starting with a WordPress security checklist that you can implement to protect your site today.
1. Understand Basic WordPress Security Themes
Before changing anything on your site, you’ll want to understand the basic themes of WordPress security:
- Limit access – limit access to your site, both via intended methods (user accounts) and unintended methods (vulnerabilities).
- Contain issues – if a malicious actor does get access, you want to limit the damage that they can do.
- Only use trusted third parties – while the WordPress core is secure, every extension you add to your site is a potential vulnerability.
2. Promptly Apply WordPress Updates
To protect your site from emerging security vulnerabilities, it’s essential to promptly apply WordPress core updates, plugin updates, and theme updates. This is especially true of security updates, which you should apply immediately*.
*Security updates have two dots in the version number – e.g. 5.9.1. You can wait to apply major feature updates, which only have a single dot – e.g. 5.9.
3. Use Strong Passwords for Everything
Using strong, unique passwords for your WordPress Admin account, hosting account, and other tools (e.g. SFTP credentials) can go a long way towards preventing brute force attacks and other types of login-based attacks.
To safely store passwords, you can use a password manager such as Bitwarden or LastPass. These password managers can also help you generate unique passwords.
4. Use Trusted Plugins
Only install plugins from trusted developers who are still actively maintaining the plugin to account for new WordPress releases and newly discovered vulnerabilities.
5. Secure Your Computer
Make sure the computer that you use to access your WordPress site is clean. Use quality anti-virus software and perform regular malware scans.
6. Lock Down Your Login Page
In addition to using strong passwords, you can protect your login page using tactics such as limiting login attempts and two-factor authentication. You can accomplish this with free feature-specific plugins such as Limit Login Attempts Reloaded and Two Factor Authentication. Or, you can use some of the broad WordPress security plugins that we’ll discuss later in this post.
You can also change the WordPress login URL. While this doesn’t add much extra login security if you’re implementing the tips above, it can cut down on bot traffic.
7. Take Regular Backups
Taking regular backups and storing them in a long place is a huge element of WordPress security. If you have a recent backup in place, a worst-case security breach is an inconvenience instead of a catastrophe when it comes to your site’s data.
Most managed WordPress hosts offer automatic off-site backups nowadays. If not, you can use a plugin like UpdraftPlus.
8. Use Secure Hosting
Use a high-quality WordPress host that implements solid security protocols such as firewalls and malware scans. While you shouldn’t rely on your host alone, a quality WordPress host can go a long way towards securing your WordPress site.
9. Install an SSL Certificate and Use HTTPS
Make sure that you’ve installed an SSL certificate and set up your site to force all traffic to the secure HTTPS version. This ensures that any data passing between a visitor’s web browser and your site’s server is encrypted.
You can consult your host’s support team or documentation to learn how to install an SSL certificate and plugins like Really Simple SSL can help you force HTTPS traffic on your site.
10. Use SFTP and Don’t Store Passwords
Make sure you use SFTP when you connect to your site’s server, rather than plain FTP (which is unencrypted). Additionally, try to avoid storing your SFTP passwords in your FTP client unless they’re encrypted and password protected.
11. Disable XML-RPC
XML-RPC helps some apps, such as an iPhone app, connect to your WordPress site. Most people won’t ever use these apps to connect, which means that XML-RPC is just an unnecessary vulnerability vector for brute force or DDoS attacks.
For that reason, most people disable XML-RPC, which you can accomplish with a plugin like Disable XML-RPC or one of the general security plugins that we’ll discuss later.
12. Disable File Editing
By default, WordPress lets Admin users directly edit theme and plugin files from the WordPress dashboard, which is a huge vulnerability if a malicious actor ever gets access to your dashboard.
You can disable it by adding a line to your wp-config.php file.
13. Monitor for Security Issues
Putting in place regular security monitoring policies can help you catch issues before they become bigger problems. We’ll talk about proper monitoring practices later in this post.
14. Secure Key WordPress Files and Folders
Some WordPress files and folders are especially vulnerable, so you’ll want to pay special attention to securing the wp-config.php file and the wp-admin and wp-includes folders.
15. Implement Proper File Permissions
File permissions control the access that users and programs have to the files and folders on your hosting server. If they’re improperly configured, they can give malicious actors access to important files such as your wp-config.php file or .htaccess file.
To learn the proper permissions for WordPress, you can read this WordPress.org page.
16. Consider Activity Logging
Activity logging lets you keep track of what’s happening on your site, which can help you catch suspicious behavior before it becomes a major issue.
To set up activity logging, you can use a specialized plugin like WP Activity Log. Or, some all-purpose WordPress security plugins also include logging functionality.
17. Add the Latest Security Headers
HTTP security headers can help secure your site by controlling how web browsers engage with your site’s content. You’ll typically configure these at the server level – KeyCDN has a great post explaining the most important security headers.
18. Secure Your Database
Using a unique database table prefix and a unique database name can make it slightly harder for malicious actors to inject malicious content into your database, though some experts debate its usefulness. Given that this change is easy to apply, it’s still worth it even if it’s a small amount of “security by obscurity”.
19. Disable Hotlinking
Having other sites hotlink your images might not be a direct security risk, but it can have a negative effect on your server in terms of wasted resources, so it’s a good security practice to disable hotlinking.
20. Set Up DDoS Protection in Advance
Have a plan for dealing with distributed denial of service attacks. You can ask your host about what protections they have in place or add your site to Cloudflare so that you can quickly enable Cloudflare’s “I’m Under Attack” mode if needed.
What Are the Risks When a Site Gets Breached?
There are three main types of risks if your site gets breached…
Risks to Your Web Visitors
If you store data about your visitors, malicious actors could get access to all of that information, which could cause issues with identity theft or financial theft depending on the data that you store.
Malicious actors could also try to trick users into downloading malicious files and infecting their computers.
Risks to Site Owners
A security breach can cause direct problems in the form of lost data, wasted time, and site unavailability. If you don’t maintain regular backups (which hopefully isn’t the case after you’ve read this guide), you might even lose your entire site and need to rebuild from scratch.
A breach can also cause less tangible issues, such as a loss of trust with your visitors or general reputational damage.
Risk to Other Sites
If you’re using shared hosting and/or hosting some of your other sites on the same hosting account, one site getting breached can quickly spread to other sites if the sites aren’t tightly isolated from one another. In this way, having one site infected can act like a domino to take out other sites, even if those sites would otherwise be secure.
How to Tell If Your WordPress Site Has Been Hacked
There are two ways that you can find out your site has been hacked:
- Reactive signs – you discover an issue because you see the problem on your site.
- Proactive signs – your security monitoring protocols alert you to the issue before it manifests on your site.
Ideally, you want to use tools that let you proactively fix issues, rather than waiting for them to become a problem. That way, you can minimize the damage to your site.
Reactive Signs of Hacking
- Browser alert – most browsers will display a warning if you visit an infected page. If that happens when you visit your own site, you know that you have a problem.
- Search engine alert – Google will also alert visitors if they click on a link that leads to an infected site. It says something like “This site may be hacked”.
- Webmaster services – if you use Google Search Console, Google will alert you to security issues if you go to Security & Manual Actions → Security issues.
- Web visitors – if web visitors encounter malicious content, they might tell you directly.
Proactive Signs of Hacking
- Malware scanner – a malware scanner can detect malicious code on your server even if it hasn’t started affecting the frontend of your site.
- File integrity checks – if core WordPress files don’t match the official versions, that’s a sign that something could be wrong on your site. Most security plugins will automatically alert you if a core file has been modified.
- Traffic monitors – monitoring your WordPress site’s traffic will help you detect irregularities as they happen.
The Wordfence plugin offers WordPress security scans
Three Best WordPress Security Plugins and Tools
If you want some extra peace of mind when it comes to WordPress security, you can consider using a dedicated WordPress security plugin or service.
While these tools don’t completely eliminate the need to be vigilant, they can handle most WordPress security best practices for you.
Here are three of the best:
1. Wordfence

Wordfence is the most popular WordPress security plugin at WordPress.org. It has a comprehensive feature set that can protect and monitor all areas of your site’s security:
- Web application firewall (WAF) to proactively block threats before they can harm your site. Includes a constantly updating set of definitions to block emerging threats.
- Malware and security scanning to detect infections or security vulnerabilities.
- Login security features including limiting login attempts, two-factor authentication, leaked password protection, XML-RPC disabling/hardening, and more.
- Real-time logging to detect malicious actors.
- Notifications to instantly alert you to potential issues on your site.
- Many other smaller hardening tactics including file change detection.
- Central security dashboard that lets you manage the security of multiple sites from one spot.
There’s a free version at WordPress.org and Wordfence Premium starts from $99.
2. Sucuri
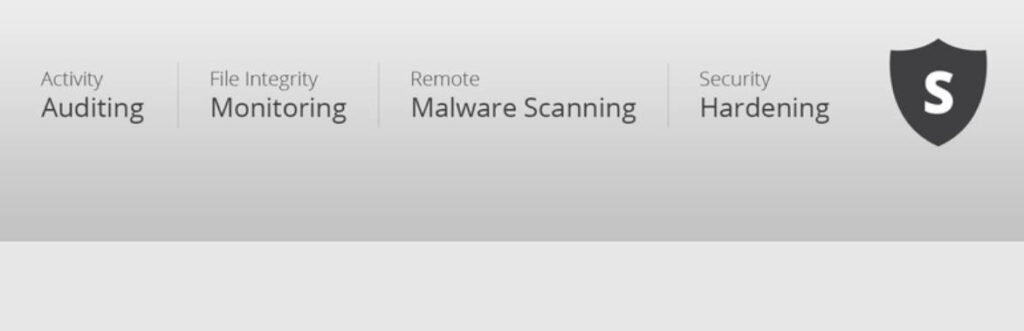
Sucuri is two things:
- A free plugin at WordPress.org that implements basic security hardening practices.
- A paid firewall service that sits in front of your server and blocks malicious traffic before it can get to your site.
For the best protection, you’ll want to use both tools.
The free Sucuri plugin implements the following security hardening features:
- File integrity monitoring
- Audit logs
- Automatic blacklist monitoring
- Basic hardening options such as disabling file editing and blocking certain PHP files
- Failed login monitoring to detect brute force attacks
- Automatic security alerts via email
To use the firewall service, you’ll change your domain’s nameservers to Sucuri and Sucuri’s firewall will protect your site at the network level.
The Sucuri plugin is free but the firewall starts at $10 per month. You can also pay for a full website security plan that includes malware cleaning and removal. Those plans start at $200 per year.
3. iThemes Security
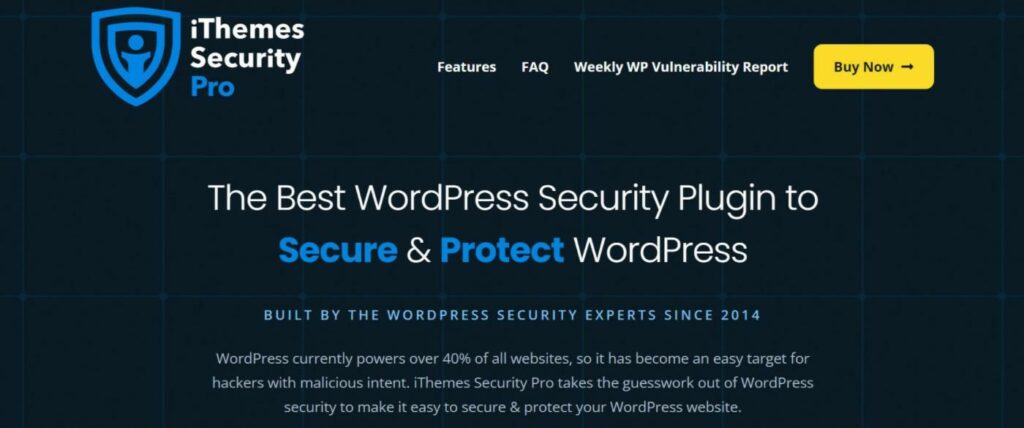
iThemes Security is another popular tool that can help you harden your site and monitor it for security issues.
Here’s what it can help with:
- Site scanner will automatically detect known vulnerabilities on your site.
- Login protection including two-factor authentication, limiting login attempts, trusted devices, strong password requirements, and more.
- Security logs including security event logging and user activity logging.
- File change detection to see if core files have been modified.
- Email notifications to instantly alert you to potential security issues.
- General WordPress hardening including disabling XML-RPC, disabling file editing, file permissions check, and more.
One feature that iThemes Security does not offer is a firewall – the developers recommend pairing it with Sucuri’s firewall service if you want a firewall.
While there is a limited free version of iThemes Security at WordPress.org, you’ll want iThemes Security Pro for the best protection. It starts at $80.
Focus On These Three Things for the Biggest WordPress Security ROI
Like a lot of things in life, WordPress security follows the 80/20 Pareto principle. That is, focusing on nailing a few fundamental WordPress security tactics will get you most of the way to having a secure site.
So while we certainly think it’s important to follow the WordPress security checklist that we shared above, focusing on just three areas will protect you from most issues with WordPress security.
Let’s go through them…
1. Plugins
While the WordPress core software is secure (as long as you keep it updated), plugins introduce variables that the core team can’t control for, which makes them one of the biggest attack vectors for malicious actors.
However, plugins are also an essential part of WordPress, so not using them isn’t a realistic option.
Here are three ways to continue benefiting from plugins while greatly minimizing your risks:
- Avoid abandoned plugins – if a plugin is no longer maintained, that means there’s no one there to fix newly discovered issues and keep it compatible with newer versions of WordPress.
- Only buy from reputable developers – use trusted developers like HeroThemes who follow WordPress security best practices and stay on top of emerging threats.
- Update regularly – even the best plugins from the best developers can sometimes have newly discovered vulnerabilities. Quality developers will patch these vulnerabilities before they become an issue – as long as you promptly update.
2. Brute Force Attacks
Brute force attacks are a common attack vector that rely on getting into your site via the login page. It doesn’t matter how secure the rest of your site is – if a malicious actor can guess your username and password, they have the keys to the front door.
Here’s how to protect yourself:
- Use strong, unique passwords – choose a strong password for all your accounts and don’t reuse the same password in multiple places.
- Limit login attempts – stop people from brute-forcing your login page by limiting failed login attempts and/or adding a CAPTCHA.
- Consider two-factor authentication – for even more security, you can consider using two-factor authentication via SMS or ideally a smartphone app or hardware key.
- Unique username – don’t use “admin” as your username and try to make your username hard to guess.
3. Hosting Account
Your WordPress site could be perfectly locked down; but if a malicious actor gets access to your hosting account, they can do pretty much whatever they want to your site.
To stop this, it’s essential to lock down your hosting account and server as well:
- Use strong passwords – as with your WordPress account, use strong, unique passwords for your hosting and SFTP accounts.
- Enable two-factor authentication – most hosting providers support two-factor authentication – take advantage of it.
- Use SFTP – always connect over SFTP and not unencrypted FTP.
- Don’t store SFTP passwords – don’t store unencrypted SFTP passwords in your FTP client.
Monitoring, Identifying, and Fixing WordPress Security Breaches
If you implement all of the WordPress security tactics above, you should hopefully never have to deal with a security breach.
However, it’s always possible for something to slip through the cracks, which is why it’s important to have a plan in place to detect and fix security issues.
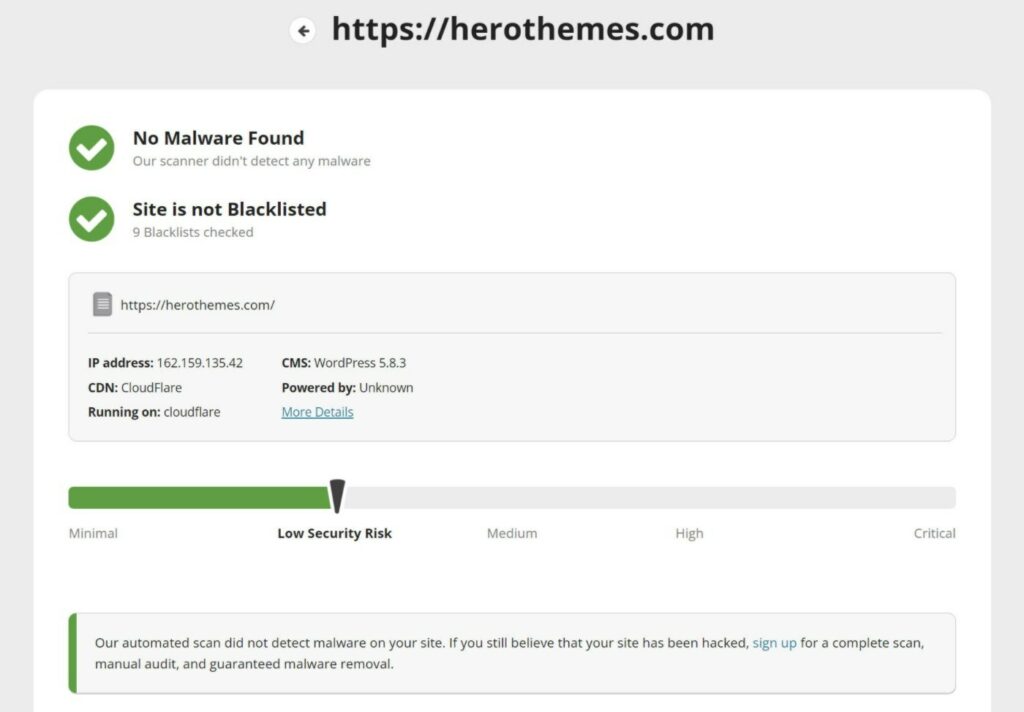
Monitoring for Vulnerabilities
- Scan your site – use tools like Sucuri SiteCheck to catch blacklist issues and scan your server with a security plugin.
- Google Search Console – pay attention to warnings in the security issues section.
- Use Google site command in search – search for site:yoursite.com to see if Google has indexed content that looks malicious. This could be content you didn’t create or content with weird titles/meta descriptions.
- Activity log – browse your site’s activity log to catch suspicious activity.
- Check analytics – look for unexplained dips or peaks in your traffic analytics.
- .htaccess file – pay attention to changes to your .htaccess file, as this is where a lot of actors will place malicious redirects or set up user-agent rules to hide their SEO spam from human visitors.
Identify Issues
Once your monitoring efforts have detected something going wrong, it’s time to identify the specific issue on your site so that you can fix it and get your site working. To do this, you can use a security plugin to scan your site and identify malicious files and backdoors.
Fixing Your Site
Once you’ve identified the specific problem, it’s time to fix your site.
There are a few different routes that you can take here depending on the severity of the infection and your knowledge level:
- Use a security plugin – many security plugins offer one-click fixes, either by cleaning the file or rolling back your site to a clean version.
- Hire an expert – if you feel overwhelmed, you can pay for an expert service like Sucuri’s Website Security or Wordfence Site Cleaning Services.
- Perform a manual cleanup – if you have the technical knowledge, you can clean your site manually – MalCare has a detailed guide on how to perform a manual cleaning.
If your site has been blacklisted by Google, you’ll also want to request a review after cleaning your site. You can do this from the Security Issues section in Google Search Console.
Keep Your WordPress Site Secure
WordPress is secure, but the ways in which people use WordPress aren’t always secure.
Taking a little time now to create a proactive plan for WordPress security will pay dividends in the form of a secure site and avoiding the need to deal with a breach in the future.
You can implement the tips from this post and follow a WordPress security checklist like Wordfence’s checklist. If you’d like a helping hand, you can also get help from a developer or hire a WordPress maintenance service.
WordPress security also isn’t something you’re alone in. You have the entire WordPress community on your site helping you create more secure sites.
Here at HeroThemes, we focus on creating secure, reliable plugins and themes that let you extend your WordPress site while keeping it secure. There are heaps of other developers doing the same.
If you stick to extensions like these and follow other security best practices, you can enjoy the benefits of a secure WordPress site.


